Are you interested in finding 'dtls essay'? All the details can be found here.
Table of contents
- Dtls essay in 2021
- Dtls essay 02
- Dtls essay 03
- Dtls essay 04
- Dtls essay 05
- Dtls essay 06
- Dtls essay 07
- Dtls essay 08
Dtls essay in 2021
 This picture demonstrates dtls essay.
This picture demonstrates dtls essay.
Dtls essay 02
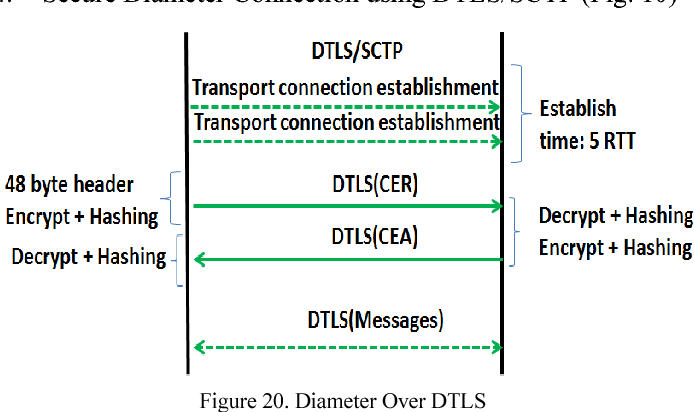 This image representes Dtls essay 02.
This image representes Dtls essay 02.
Dtls essay 03
 This picture illustrates Dtls essay 03.
This picture illustrates Dtls essay 03.
Dtls essay 04
 This picture illustrates Dtls essay 04.
This picture illustrates Dtls essay 04.
Dtls essay 05
 This picture illustrates Dtls essay 05.
This picture illustrates Dtls essay 05.
Dtls essay 06
 This image shows Dtls essay 06.
This image shows Dtls essay 06.
Dtls essay 07
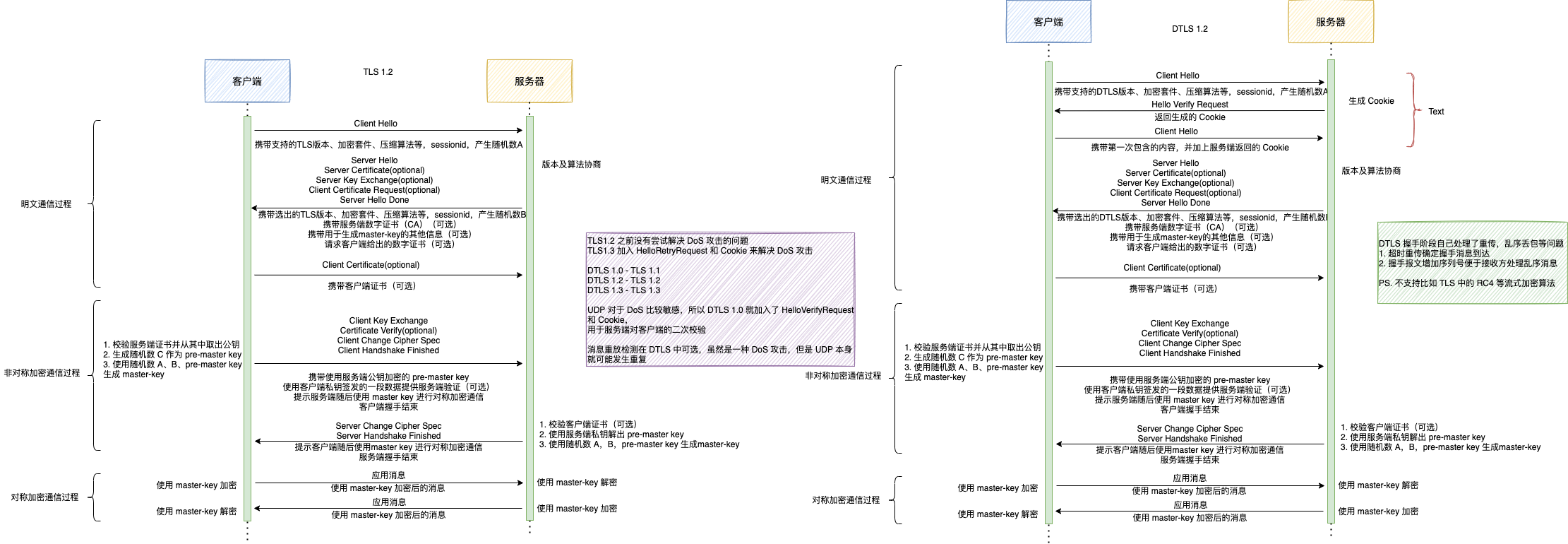 This picture shows Dtls essay 07.
This picture shows Dtls essay 07.
Dtls essay 08
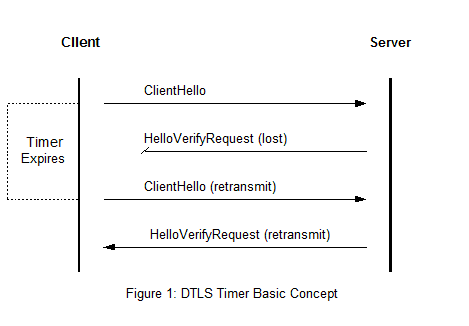 This picture illustrates Dtls essay 08.
This picture illustrates Dtls essay 08.
What is the design philosophy of DTLS protocol?
The basic design philosophy of DTLS is to construct “TLS over datagram transport”. Datagram transport does not require nor provide reliable or in-order delivery of data. The DTLS protocol preserves this property for application data.
What's the difference between a TLS and a DTLS?
• DTLS provides UDP based transport while using TLS security. As a result, as with UDP, it does not re-order or re-transmit packets. • Following table mentions handshake difference between TLS and DTLS.
Is the datagram transport layer security ( DTLS ) protocol designed?
There are applications that utilize UDP [RFC0768] as a transport and to offer communication security protection for those applications the Datagram Transport Layer Security (DTLS) protocol has been designed.
Which is an application that can use DTLS?
DTLS can be used in many applications designed based on datagram protocols. These applications include IM application, gaming application etc. Now there are quite a few libraries have support of both DTLS v1 and DTLS v1.2. Some of them are OpenSSL, NSS. Java 9 is also planning to add support of DTLS.
Last Update: Oct 2021