Do you ask for 'security log book report'? All material can be found on this website.
Table of contents
- Security log book report in 2021
- Security guard log book
- Security log book template
- Types of security guard reports
- Monthly security report sample
- Security log book fnaf
- Security log book pdf
- Security guard daily log template
Security log book report in 2021
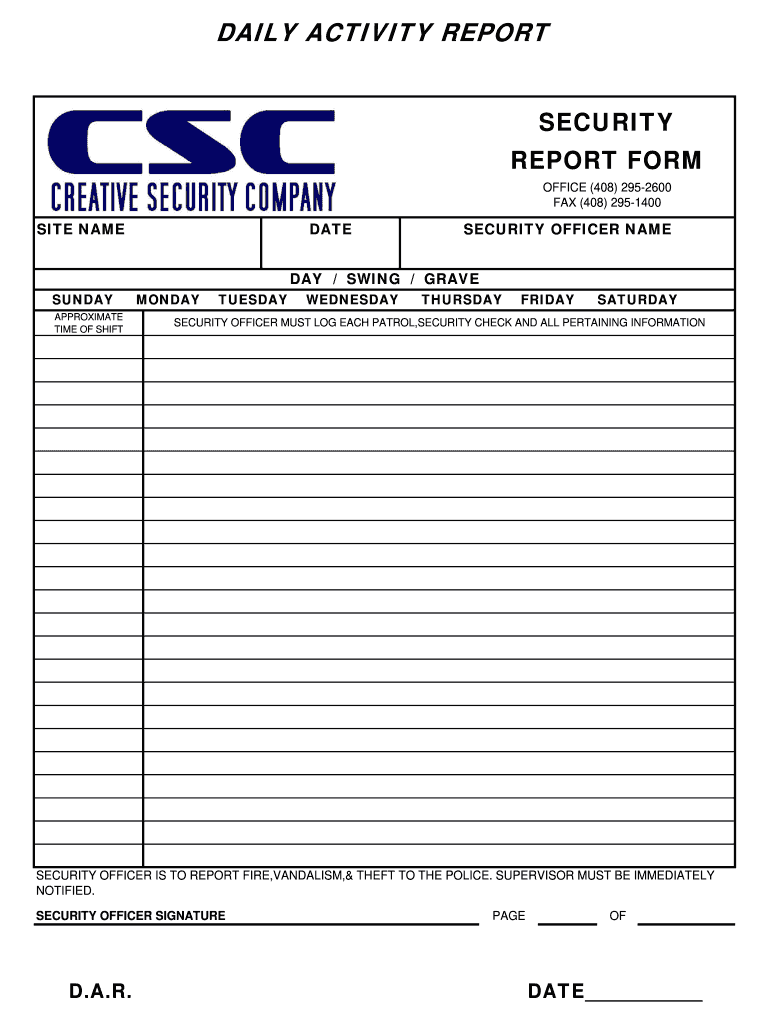 This image illustrates security log book report.
This image illustrates security log book report.
Security guard log book
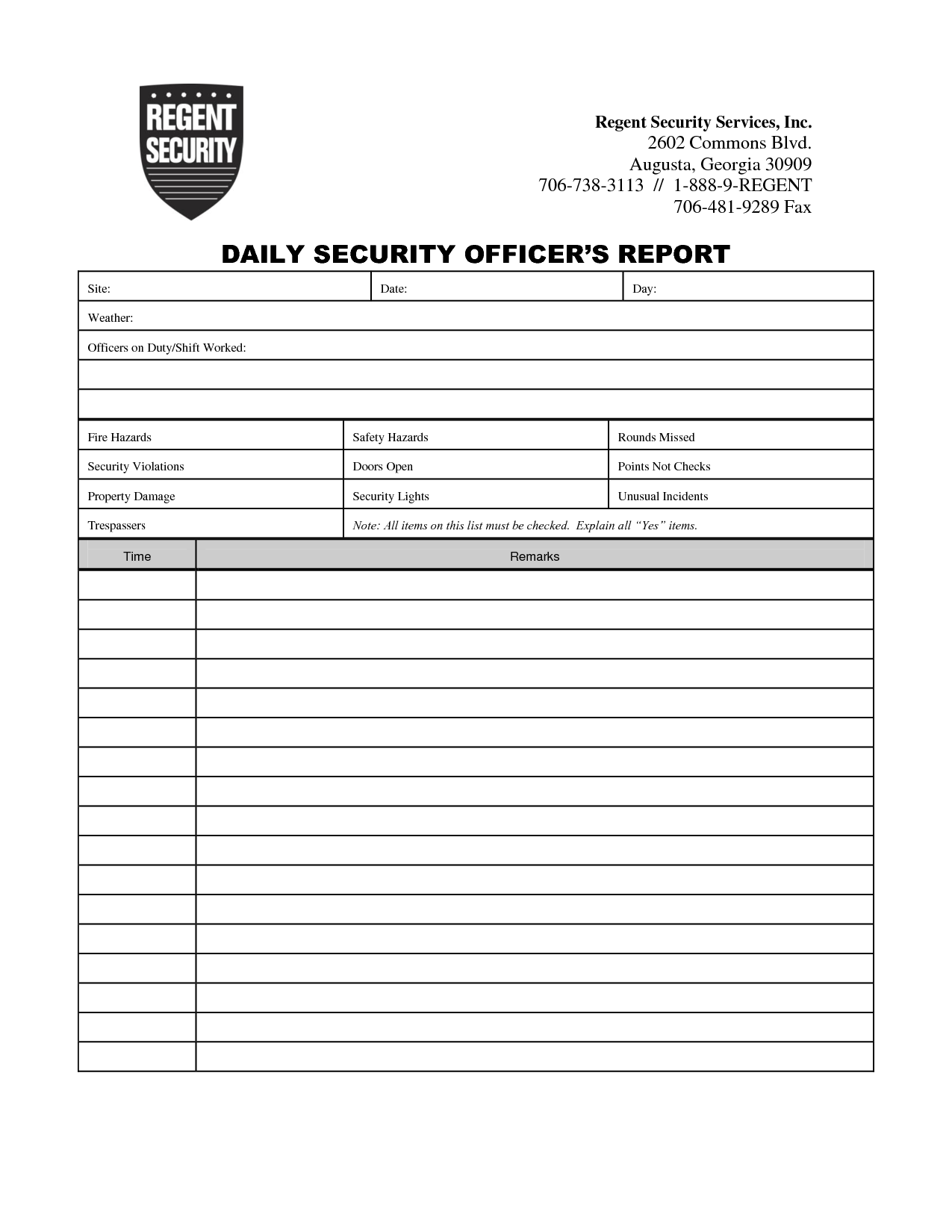 This picture shows Security guard log book.
This picture shows Security guard log book.
Security log book template
 This image illustrates Security log book template.
This image illustrates Security log book template.
Types of security guard reports
 This picture shows Types of security guard reports.
This picture shows Types of security guard reports.
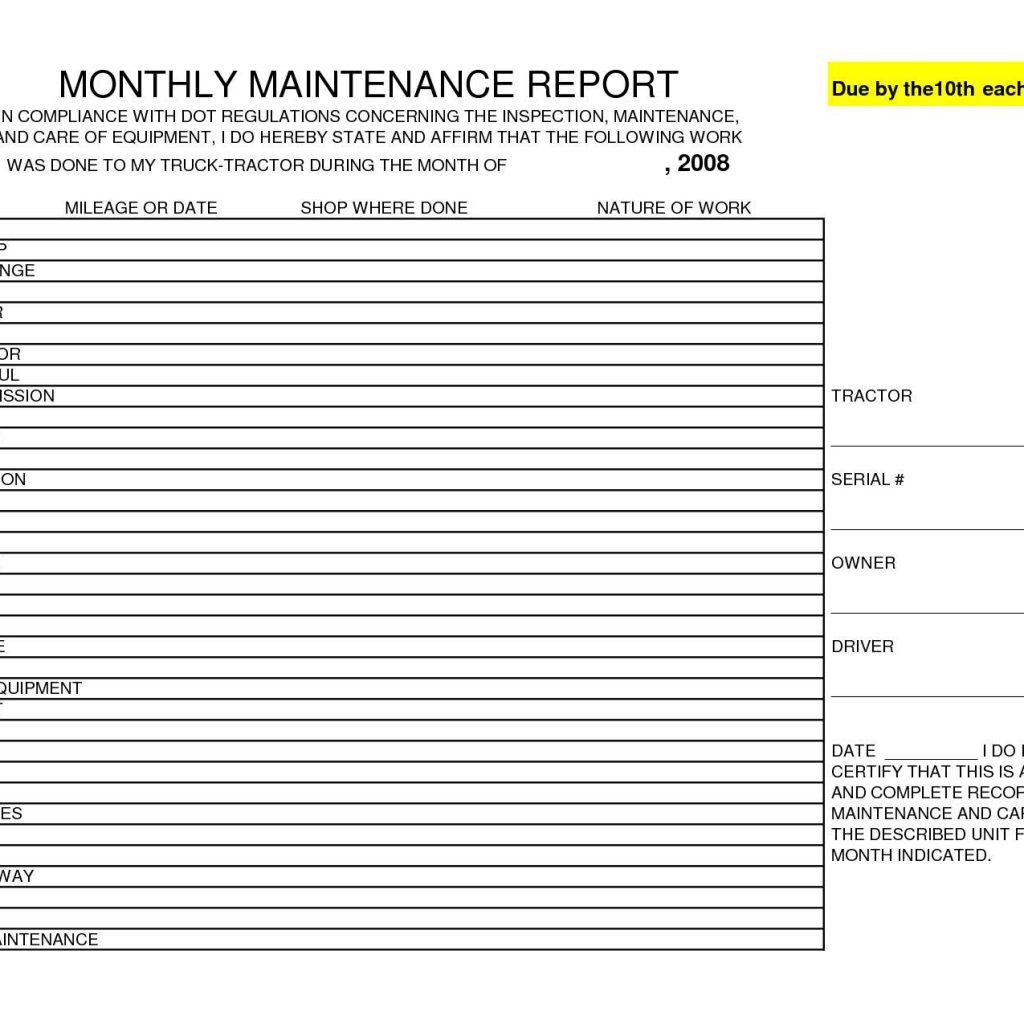
Monthly security report sample
 This picture illustrates Monthly security report sample.
This picture illustrates Monthly security report sample.
Security log book fnaf
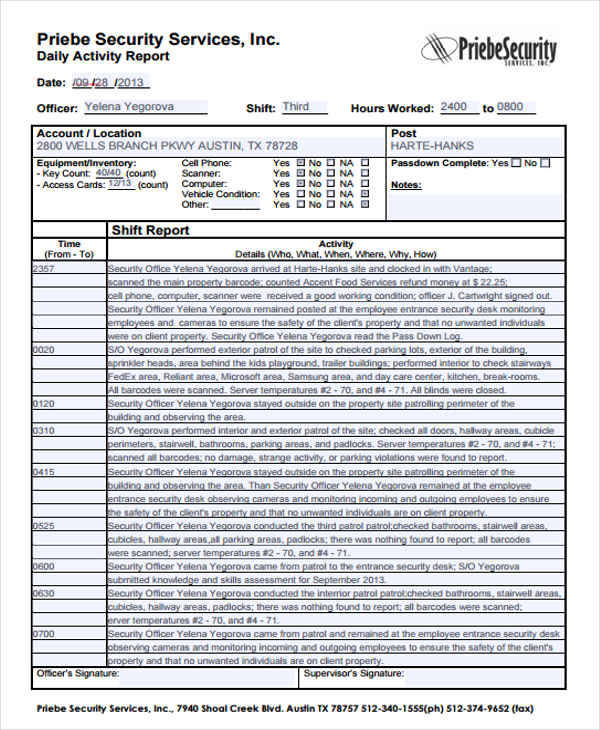 This image shows Security log book fnaf.
This image shows Security log book fnaf.
Security log book pdf
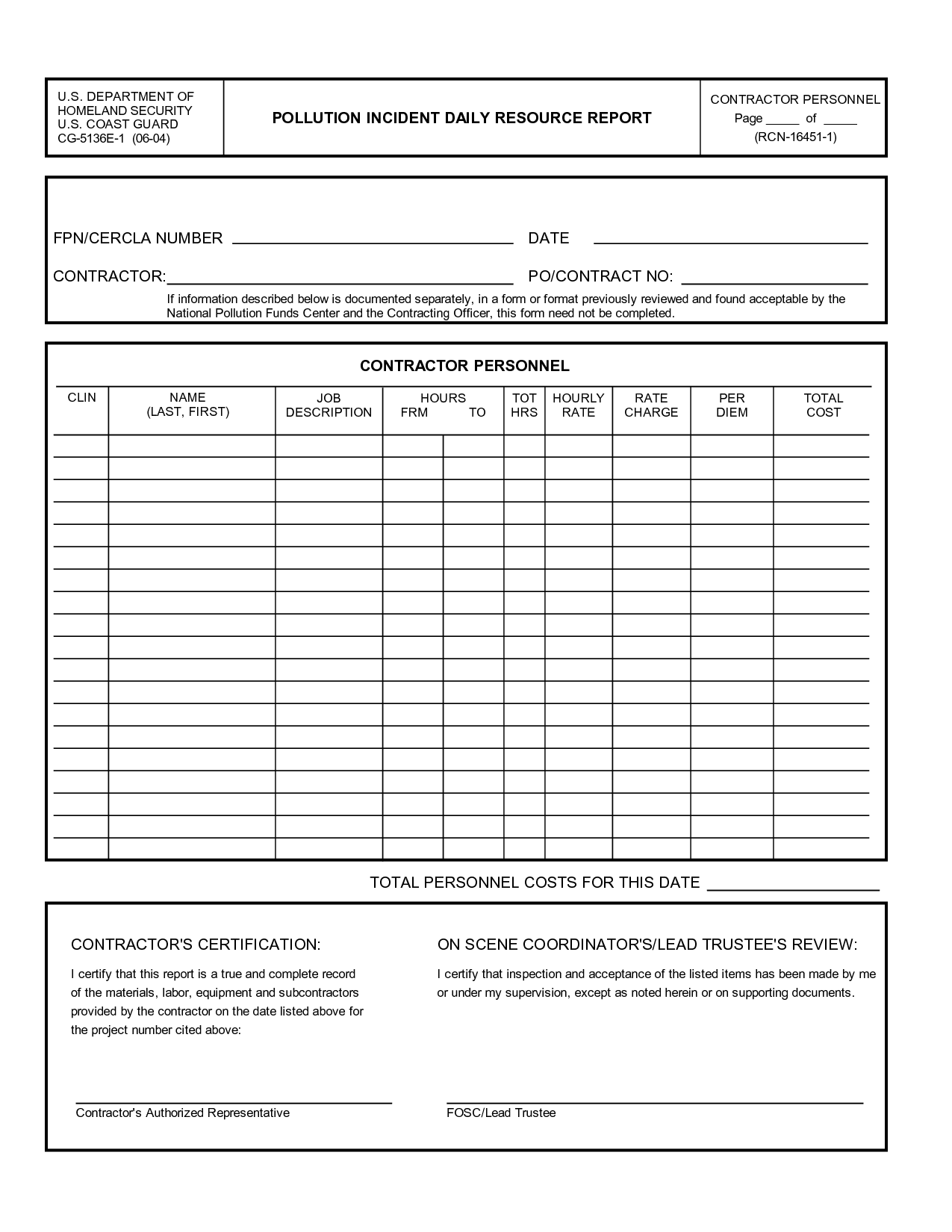 This image shows Security log book pdf.
This image shows Security log book pdf.
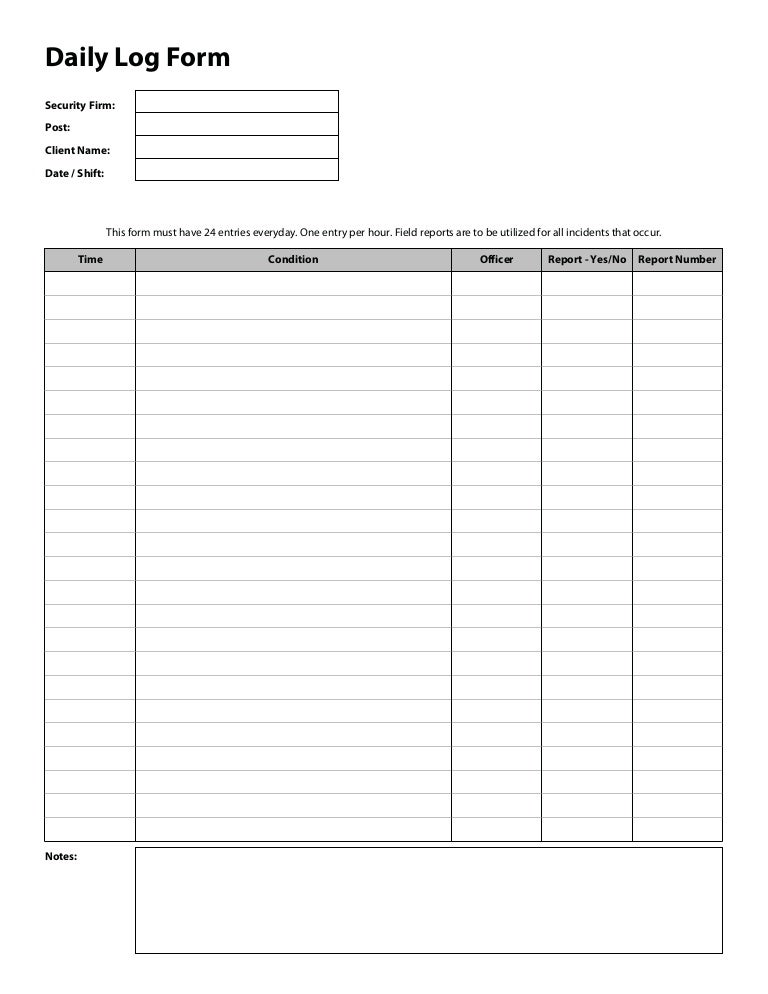
Security guard daily log template
 This picture shows Security guard daily log template.
This picture shows Security guard daily log template.
How does daily log form for security guards work?
With our Security Guard Daily Log Form you have the ability to regiment the frequency of log entries, the post (s) that should utilize the form and you are alerted that there is a field report pending or written on a particular condition.
What should be included in a security log?
In my opinion, you want a log to include the time, security officer, category of action (Mobile Patrol, Foot Patrol, Arrest, etc), summary information section and an action taken section. The way I look at it, you have to justify your job through documentation so the more detail the better unless your boss says otherwise.
When do security guards write their daily report?
Many officers write their reports of daily activities at the close of the shift, which makes it tedious and most of the time imprecise. Security officers must be extremely observant and have detailed guidance.
What should be included in a security officer daily action report?
As a security officer, your observations show your client what you are doing during your shift and protect your client should an incident occur. For these reasons, your Daily Action Report must be accurate and detailed. The DAR is also referred to as the Shift Report or the Patrol Log.
Last Update: Oct 2021
Leave a reply
Comments
Myrtie
27.10.2021 00:21Use of goods and services this report equally a guide to help deliver day-and-night improvements to your cyber resilience scheme in a covid world. With hundreds of chapters across the globe, asis is recognized as the premier source for learning, board-certification, networking, standards, and research.
Vicie
27.10.2021 12:38When on the attestant stand, the certificate guard may be. O open: the modification request is presently open but has not yet been addressed.
Leane
22.10.2021 12:28The proper authorities testament take care of the investigative employment when needed. We apprize your help stylish keeping our systems and products certified.